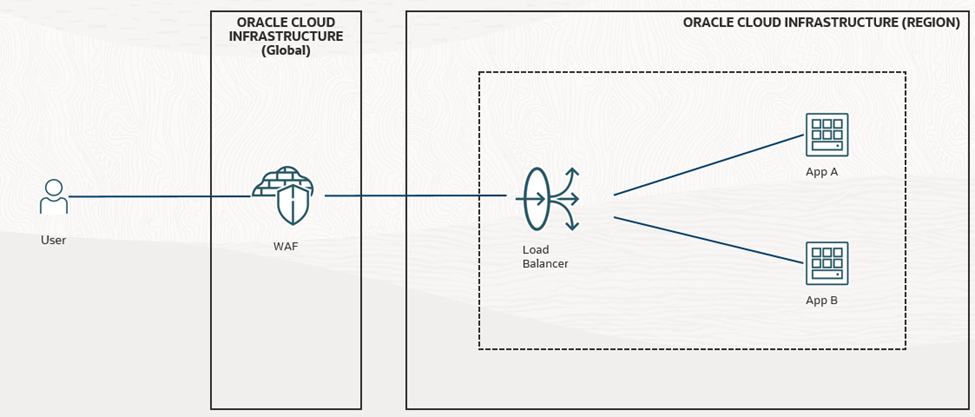
Oracle Cloud Infrastructure (OCI) includes a Web Application Firewall (WAF) service that acts as a reverse proxy in front of your applications. A WAF inspects inbound and outbound traffic flows before they arrive at your origin servers and monitors responses before they leave the server. This extra security layer filters malicious and unwanted traffic with built-in features. OCI’s WAF can manage multiple types of threats:
Origin management – define one or more origin servers for the application being protected.
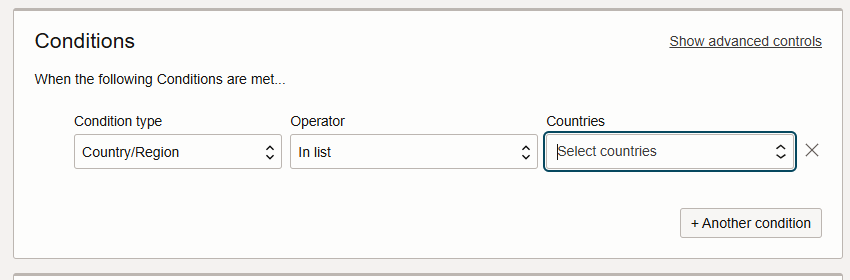
Access control – granular rules to allow or block traffic based on IP addresses, countries/regions, request headers, or URI patterns.
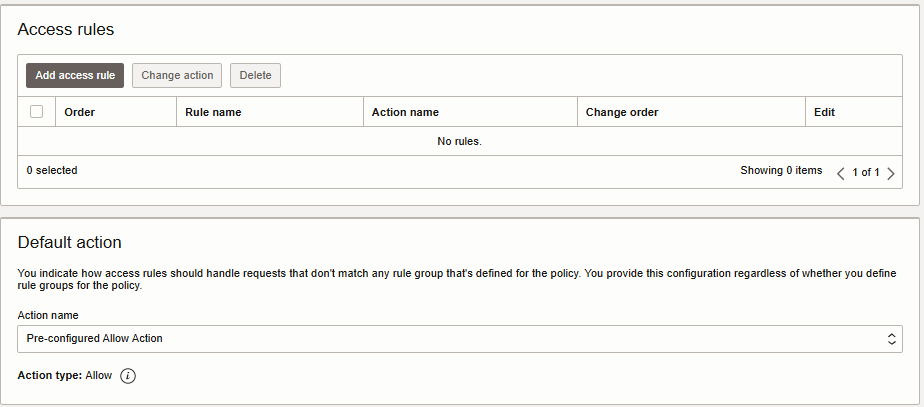
Protection rules – pre-configured policies (over 250 OWASP-aligned rules) to defend against common attacks such as SQL injection and cross-site scripting.
To know about supported Protection Rules, click here.
Unlike a traditional firewall, the OCI WAF scales elastically and offers centralized rule enforcement across your tenancy. It sits in front of your load balancers or endpoints, inspecting requests and responses, and then forwards legitimate traffic to the origin. The following sections present a step-by-step implementation based on Oracle’s official guidance and practical walkthroughs.
Prerequisites
To begin using the WAF service, you must have the following available:
- Ensure that you have the Required IAM Service Policy permissions.
- We recommend using a separate compartment for the WAF policy to facilitate easier and more secure management.
- A main webapp domain.
- IP address of the LBaaS or other public-facing endpoint of the application.
- The WAF service only supports traffic on ports 80/443; however, after requests reach the WAF on ports 80/443, we’re able to send the requests to your origin server on any port necessary
Step 1 – Create a WAF policy zone
- Select the region and compartment where the policy should be maintained (there is no constraint around the WAF co-existing with Load Balancer or other application resources in Oracle Cloud Infrastructure.
- Open the navigation menu and select Identity & Security. Under Web Application Firewall, select Policies.
- Click Create WAF Policy.
- Look at the bottom of the Basic Information page for the following:
Use legacy workflow here if you need to secure your non-OCI web applications.
- Click the link to display the Create Edge Policy dialog box.
- Complete the following:
- Name: A unique name for the policy.Domains:
- Primary Domain: The fully qualified domain name (FQDN) of the application where the policy will be applied.Additional Domains: (Optional) Subdomains where the policy will be applied.
- Origin Name: A unique name for the origin.URI: Enter the public-facing endpoint (IPv4 or FQDN) of the application.HTTPS Port: The port used for a secure HTTP connection. The default port is 443.HTTP Port: The HTTP port the origin listens on. The default port is 80.Headers: (Optional)
- Header Name: The name displayed in the HTTP request header and the header value that can be added and passed to the origin server with all requests.Header Value: Specifies the data requested by the header.
- Tags: If you have permissions to create a resource, then you also have permissions to apply free-form tags to that resource. To apply a defined tag, you must have permissions to use the tag namespace. For more information about tagging, see Resource Tags. If you’re not sure whether to apply tags, skip this option or ask an administrator. You can apply tags later.
- Name: A unique name for the policy.Domains:
- Click Create WAF Policy. The WAF Policy overview appears. Expect the policy to become active within 15 minutes of creation.
See Managing Edge Policies for more information.

Step 2 – Configure access-control rules
The real power of OCI’s WAF lies in its ability to define custom access rules. In this example, we block all traffic from the United States, except for a specific IP address. The same pattern can be adapted for other countries or IP ranges. To create a rule:
- Open the navigation menu and click Identity & Security. Under Web Application Firewall, click Policies.
- On the Policies page, select the compartment that contains the policy.
- (Optional) Filter the listed policies by name, state (status), policy type (Edge policy), or creation date.
- Click the name of the Edge policy to which you want to add an access rule.
- On the policy details page, under Edge policy, click Access control.
- Click the Access rules tab.
The Access rules list appears. For more information, see Access Rules for Edge Policies.
- Click Add access rule.
- Provide the following information:
- Name: Enter a name for the access rule.Action: Select one of the following options to determine the response to a request when the rule is matched:
- Log and allow: A log is created for all matched requests, and no further action is taken.Detect only: A detection alert is created for all matched requests, and no further action is taken.Block: All matched requests are blocked, and a browser page for the selected response code is returned.
- Block action: Select the action that’s taken when a matching request is blocked.Block response code: Select a response code that’s returned when the request has been blocked. The response code provides information indicating why the request was blocked. The default response code is 403 Forbidden.
- Redirect status code: Select the status code returned in response to redirect requests from the list.Redirect URL: Enter the URL address to redirect the request to.
- CAPTCHA title: Enter the text for the CAPTCHA page title.CAPTCHA header: Enter the text that appears before the CAPTCHA image (for example, “I am not a robot”).CAPTCHA footer text: Enter the text to display after the CAPTCHA input box and before the submit button.CAPTCHA submit button: Enter the text for the Submit button (for example, “Yes, I am human.”).
- Log and allow: A log is created for all matched requests, and no further action is taken.Detect only: A detection alert is created for all matched requests, and no further action is taken.Block: All matched requests are blocked, and a browser page for the selected response code is returned.
- Header manipulation(s): Complete the following information:
- Action: Select the action to apply to the request.
- Header name: Enter the HTTP header name of the request.
- Header value: Enter the HTTP header value of the request.
- Name: Enter a name for the access rule.Action: Select one of the following options to determine the response to a request when the rule is matched:
- Click Add access rule.

Step 3 – Adding a Firewall to a Web Application Firewall Policy
Add a firewall to a web application firewall (WAF) policy to create a logical link between the policy and an enforcement point, such as a load balancer.
- On the Policies list page, select the WAF policy that you want to add the firewall to. If you need help finding the list page or the policy, see Listing Web Application Firewall Policies.
- On the WAF policy’s details page, under Policy, select Firewalls.
- Select Add firewalls.
- In the Add firewalls panel, enter the following information:
- Firewall name: Enter the name of the firewall.
- Create in compartment: Select the compartment that contains the firewall you are creating.
- Load balancer: Select the load balancer. Select Change compartment to select a load balancer from a different compartment
- Enable WAF logs: Select this option to generate logs that contain WAF security events.
Logging is an option in the Web Application Firewall service. Standard limits, restrictions, and rates apply when enabling the logging features. See Oracle Cloud Infrastructure Logging.
- WAF logs: (Optional) Apply the following configurations to all WAF logs that you enabled. You can update these settings later for individual log files in the log details See Logs and Log Groups.
- Compartment: Select the compartment where the WAF logs reside.
- Log group: Select the log group.
- Log retention: Select the length of time log entries are retained in the log file.
- Show tagging: (Optional) Add one or more tags to the firewall.
If you have permissions to create a resource, then you also have permissions to apply free-form tags to that resource. To apply a defined tag, you must have permissions to use the tag namespace. For more information about tagging, see Resource Tags. If you’re not sure whether to apply tags, skip this option or ask an administrator. You can apply tags later.
- Select Add firewalls.

Key Use Cases
Some of the use cases for a Web Application Firewall.
- Protection against cyberattacks.
- Access Control for Data Privacy Standards
- Integration with existing management systems.
- Bot Management
- Hybrid and multi-cloud protection.
Conclusion
It is essential to protect and monitor a web application against potential threats and secure it from unwanted or harmful traffic. To achieve this, we use a Web Application Firewall (WAF), which prevents malicious traffic from accessing the application.
In this post, I cover an overview of WAF, how to manage WAF in OCI, and some practical use cases. I hope this helps you better understand the concept of WAF in OCI.